Cloudflare與蘋果聯手打造更具隱私的Oblivious DNS-over-HTTPS協定
News from: Cloudflare
新的DNS標準Oblivious DNS over HTTPS(ODoH),強調隱私防護能力比DoH完備,可避免ISP或DNS解析業者窺探使用者隱私 。提供內容遞送網路、DDoS緩解與DNS服務的Cloudflare,本周宣布已與蘋果及另一美國雲端運算服務供應商Fastly共同開發了新的DNS標準,此一新標準名為Oblivious DNS over HTTPS(ODoH),奠基在DoH之上,但額外提供使用者的隱私保護,避免ISP或DNS解析業者窺探使用者隱私。
Web site: https://blog.cloudflare.com/oblivious-dns/
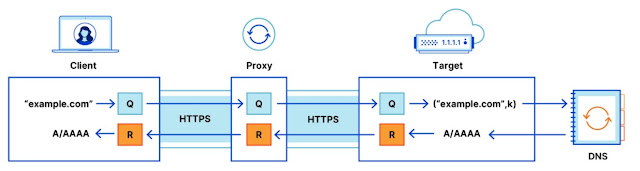
ODoH架構是在DoH上額外添增了兩個元件,一是獨立的端對端加密層,二是在客戶端與目標伺服器之間新增一個代理人,於是,客戶端傳送的是加密的網址查詢,先傳送到代理人,再傳送到目標伺服器,目標伺服器解密之後回傳使用者所要查詢的網站IP,同樣得先經過代理人,再傳送至客戶端。
There are three players in the ODoH path. Looking at the figure above, let’s begin with the target. The target decrypts queries encrypted by the client, via a proxy. Similarly, the target encrypts responses and returns them to the proxy. The standard says that the target may or may not be the resolver (we’ll touch on this later). The proxy does as a proxy is supposed to do, in that it forwards messages between client and target. The client behaves as it does in DNS and DoH, but differs by encrypting queries for the target, and decrypting the target’s responses. Any client that chooses to do so can specify a proxy and target of choice.
Together, the added encryption and proxying provide the following guarantees:
- The target sees only the query and the proxy’s IP address.
- The proxy has no visibility into the DNS messages, with no ability to identify, read, or modify either the query being sent by the client or the answer being returned by the target.
- Only the intended target can read the content of the query and produce a response.
These three guarantees improve client privacy while maintaining the security and integrity of DNS queries. However, each of these guarantees relies on one fundamental property — that the proxy and the target servers do not collude. So long as there is no collusion, an attacker succeeds only if both the proxy and target are compromised.
DNS系統的作用是將使用者所輸入的網址轉換成該站的IP位址,傳統的DNS查詢是以明文遞送,為了避免遭到中間人攻擊,近來業者開始採用DNS over HTTPS(DoH)協定,加密查詢流量,然而,DoH出現了兩個隱憂,一是DNS的集中化可能招致單點故障,其次則是就算中間人看不到使用者的查詢內容,但DNS解析器依然能夠知道哪個使用者的IP查詢了什麼網站。
就在Google及Mozilla相繼於瀏覽器中導入DoH之後,亞太網路資訊中心(APNIC)即曾質疑,DNS通常是由網路的操作者所提供,例如ISP業者、電信業者、企業主或是邪惡的公開Wi-Fi,但DoH基本上只能阻止中間人攻擊,並無法阻止DNS伺服器供應商檢視、封鎖或竄改DNS資料。而ODoH即能解決此一顧慮。
ODoH架構是在DoH上額外添增了兩個元件,一是獨立的端對端加密層,二是在客戶端與目標伺服器之間新增一個代理人,於是,客戶端傳送的是加密的網址查詢,先傳送到代理人,再傳送到目標伺服器,目標伺服器解密之後回傳使用者所要查詢的網站IP,同樣得先經過代理人,再傳送至客戶端。
因此,DoH伺服器只會看到客戶端所查詢的內容與代理人的IP位址,代理人則完全看不見查詢或回傳內容,且只有指定的目標伺服器才能讀取與回應查詢。
為了建立ODoH生態體系,包括電訊盈科、美國電信業者Equinix與荷蘭的非營利研究機構SURFnet,都已成為此一新協定的合作夥伴。
另一方面,Cloudflare也測量了基於ODoH的DNS服務是否會影響效能,在美國、加拿大與巴西測試了1.1.1.1、8.8.8.8及9.9.9.9等DNS服務的運作狀況,顯示ODoH只比DoH慢了不到1毫秒(千分之一秒)。
除了Cloudflare旗下的1.1.1.1公共DNS查詢服務已支援ODoH之外,Cloudflare、蘋果及Fastly也已開源支援Rust、odoh-client-rs、Go及odoh-client-go的測試客戶端,而Firefox技術長Eric Rescorla也說,期待於Firefox中實驗ODoH。


留言
張貼留言